every website is a potential Shadow IT application.
Every Website Is a Potential Shadow IT Application
Every Website Is a Potential Shadow IT Application
Hey There! Nice to see you!
Choose the most relevant content to your profile.
Features
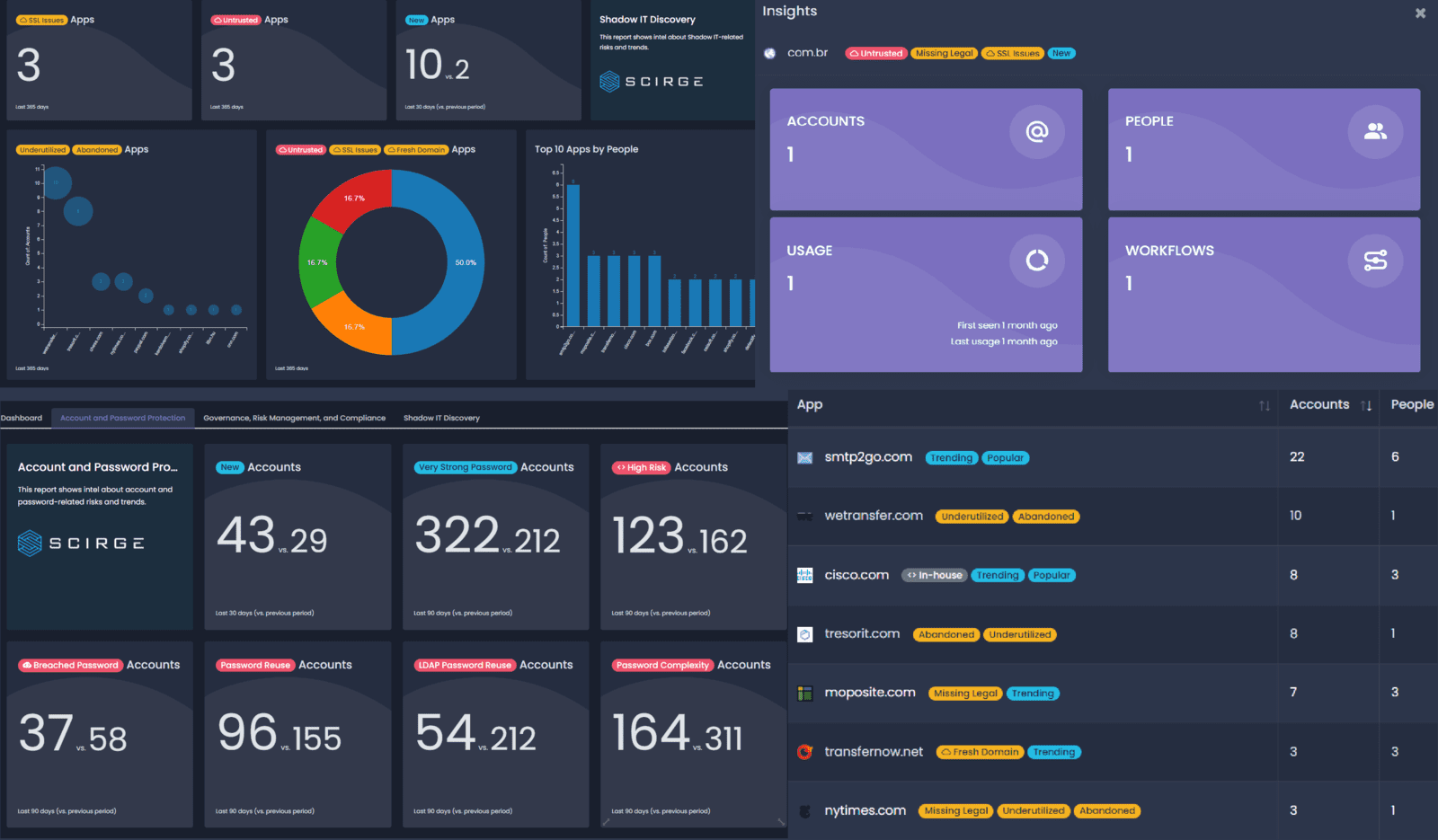
Scirge provides a unique approach to unveil and gain control over unmanaged third-party web accounts. Scirge tracks the websites employees use corporate email addresses to register on and log in to.
App and Account Discovery
Password Hygiene
Education
and Automation
Use-Cases and Benefits
Visibility for cloud apps means control over your supply chain. Manage your Enterprise Attack Surface through automation and education. Discover legacy applications, accounts, and internal threats via application and account inventories.
Create inventories for Zero Trust efforts, Data Processors, Identity Management, and Business Continuity.
No matter your regulations, managing your inventories and external assets is fundamental for compliance.
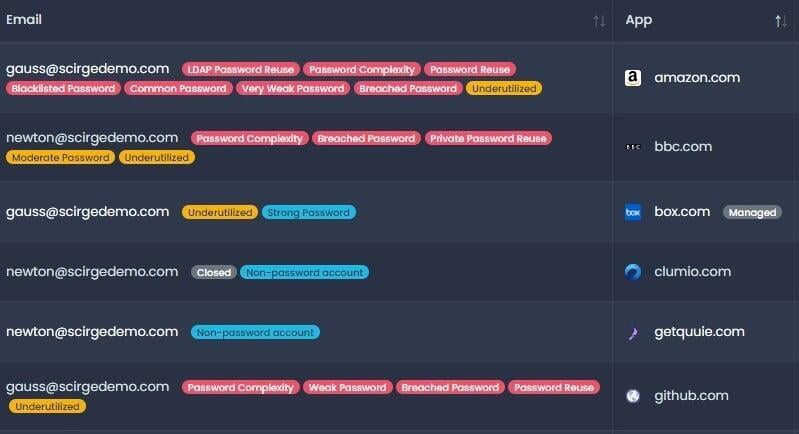
Detect phishing attacks, breached or reused LDAP and third-party passwords, weak credentials, and unmanaged accounts. Scirge provides the highest level of password hygiene because it doesn't rely upon any opt-in action from employees –it's completely transparent.
How Does Scirge Work?

The Scirge browser extension can detect any web form submission (such as logins, registrations, or any other credential submission) using centrally-managed policies without relying on a database.
A typical policy is to monitor the usage of all corporate-related email domains. Having a central dashboard of discovered accounts helps to reduce the risk of credential-related threats such as credential stuffing, password reuse or account takeover.
Join Our Webinars!
© 2022 Scirge.com, All rights reserved. www.scirge.com/privacy